PearlCTF - ShadowVault
Initial Analysis
We were given an APK file to analyze. My first step was to use apktool to decompile the application and examine its contents.
This was the basic structure of the contents inside the application. Nothing looked suspicious, and everything appeared normal at first glance.
Static Analysis
Next, I used Jadx-GUI for static analysis of the application while simultaneously starting Genymotion to observe its actual behavior.
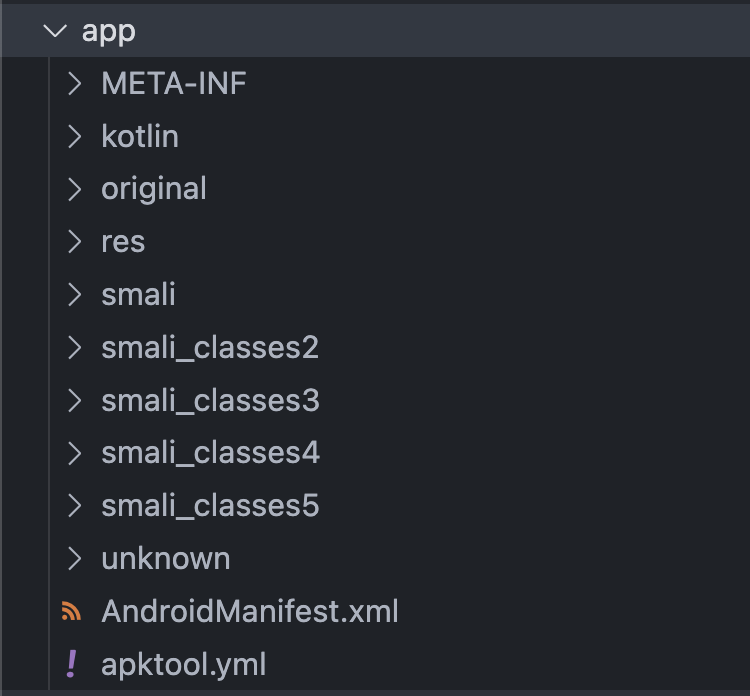
The application had nothing but this login screen. This simplicity made me suspicious that there might be more going on behind the scenes.
Dynamcis Code Analysis
I started looking for keywords like "User name" and "password" while statically analyzing the code. The only relevant information I found was this:
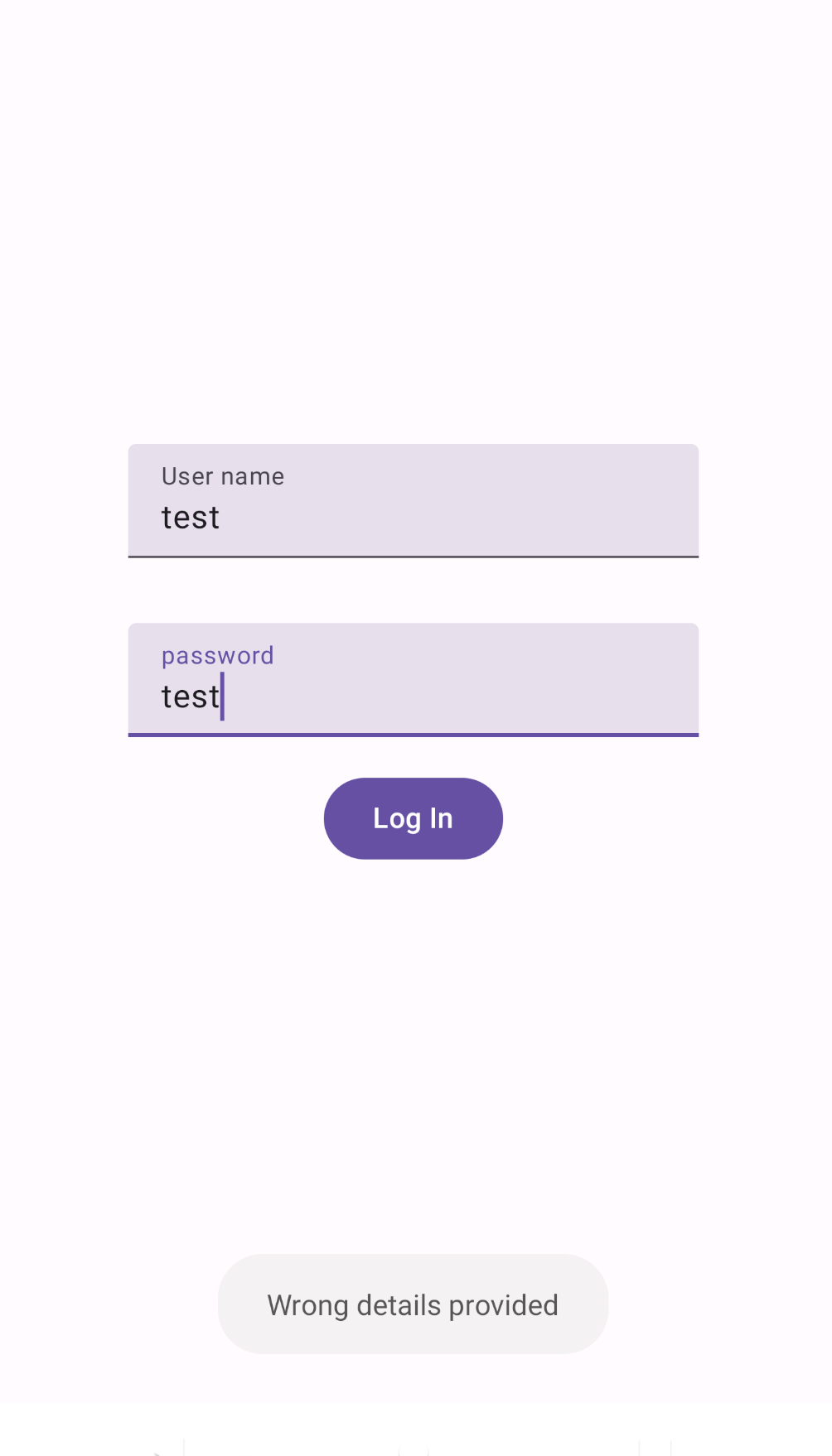
At this point, I had a thought—what if the application is actually communicating with a server in the backend? So, I started searching for patterns like "https" and "http," and luckily, I got a nice hit.
Here, you can see that the BASE_URL is set to the server-side of the organizing team. I made a ticket on Discord to ask whether the flag was on the server side or the client side, and they confirmed it was on the
server side. At this point, all I needed to find were the endpoints of the BASE_URL.
The AuthService in the context of the provided code refers to an interface that defines the API endpoints for authentication-related operations.
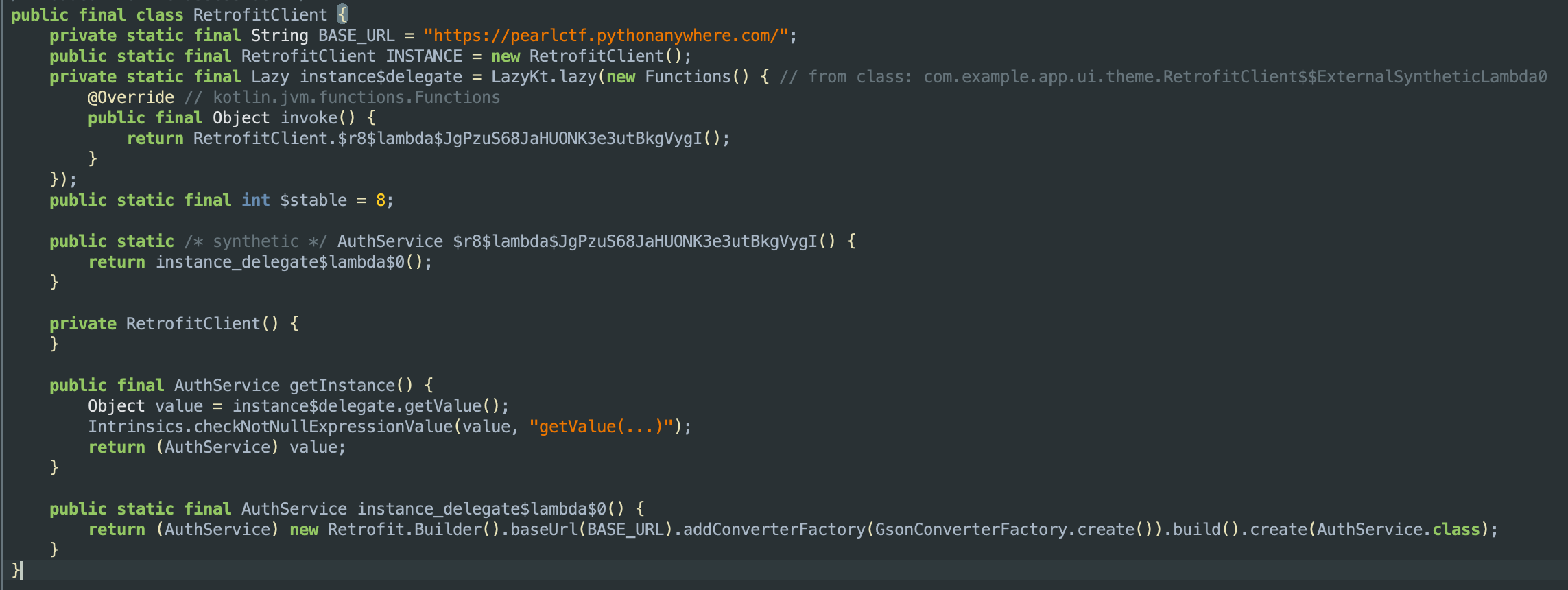
Server Communication
The AuthService was showing /location as its endpoint with a POST JSON request. I fired up Burp and sent a blank POST request to
/location, which returned this response:
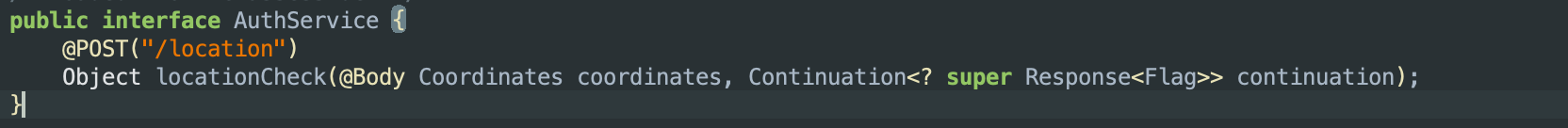
At this point, it was clear that:
- The request requires two parameters.
- We need to find the exact coordinates to get the flag.
Finding the Coordinates
I went back and searched for "Latitude" and "Longitude" (there were more than 50 results). After some searching and analyzing, I finally located the relevant code:
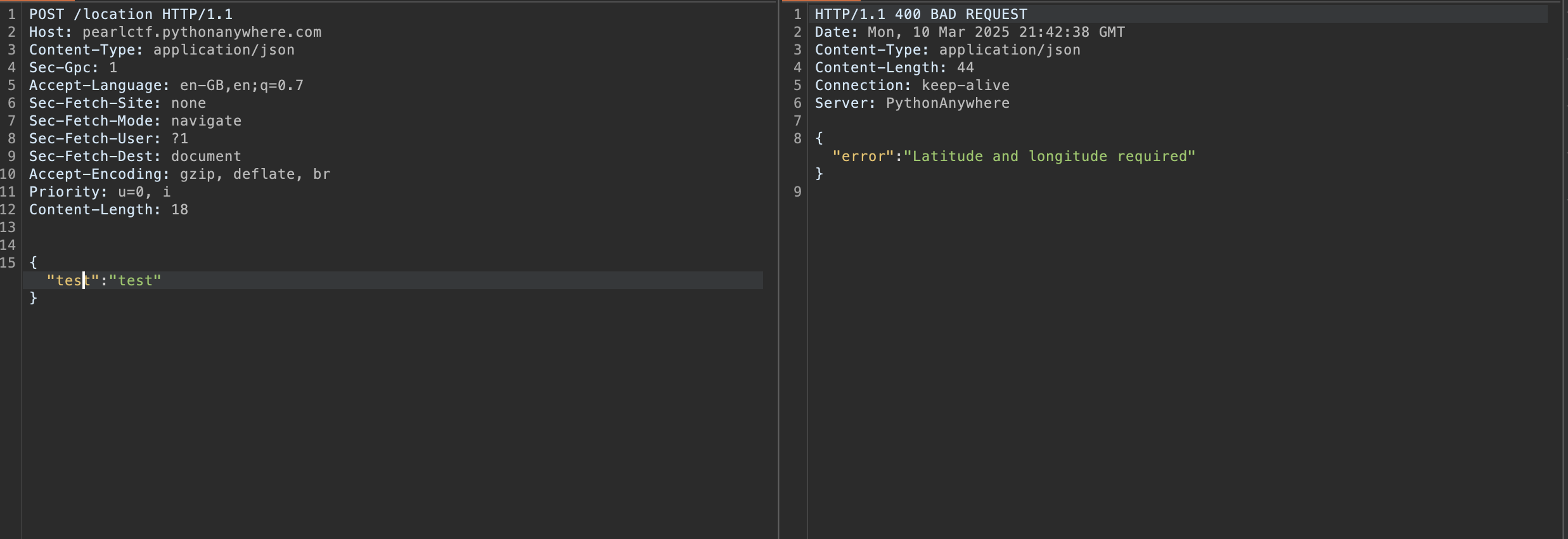
Here you can clearly see the value of Latitude being set to 100 while the value of Longitude is set as Latitude * 2.
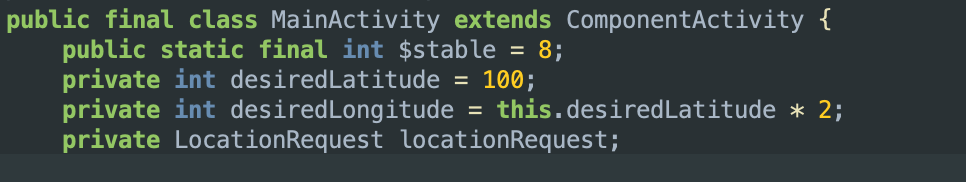
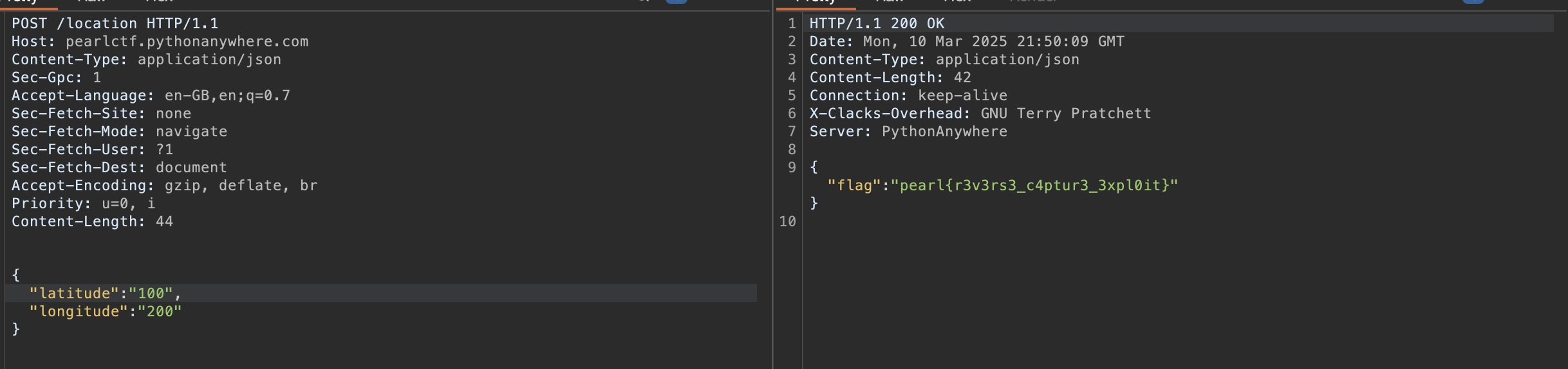
Using these coordinates in my request, I successfully obtained the flag: pearl{r3v3rs3_c4ptur3_3xpl0it}
Conclusion
This challenge demonstrated the importance of thoroughly analyzing mobile applications, looking for server communication, and understanding how the application processes and sends data. By identifying the correct coordinates hardcoded in the application, we were able to craft the proper request to the server and retrieve the flag.